Privacy & Security
Architecting secure systems that protect sensitive health and device data.
 Embedded Software
Embedded SoftwareNordic nRF52840: Is Rust a Good Fit for Embedded Applications?
Understand Rust's pros and cons on nRF52840, covering memory footprint, performance, safety, tooling, ecosystem, and C interop, to make an informed go‑no‑go decision for embedded firmware.
 Bluetooth Low Energy (BLE)
Bluetooth Low Energy (BLE)BLE Security: Where to Begin When Creating a Connected System
Start BLE security planning early by understanding pairing modes, bonding options, threat modeling, and tradeoffs that shape secure, reliable connected systems.
 Bluetooth Low Energy (BLE)
Bluetooth Low Energy (BLE)BLE Sniffers for Debugging: When and Why to Upgrade Your Tools
Learn how BLE sniffers help uncover issues in Bluetooth Low Energy communication. This article covers when to use them, compares tool options, and explains how they support debugging and development across simple and complex connected device workflows.
 Mobile Apps
Mobile AppsArchitecting iOS and Android Apps for IoT BLE Systems
Learn how to architect cross-platform BLE apps for iOS and Android. This guide covers organizing code, managing connections, and structuring reusable logic for scalable Bluetooth development.
 Bluetooth Low Energy (BLE)
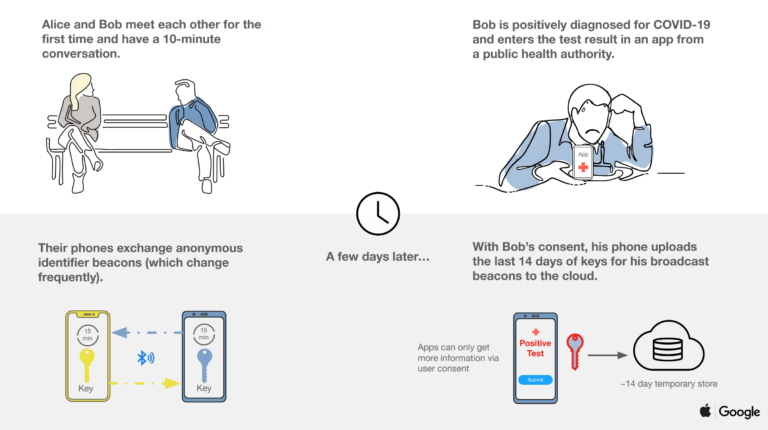
Bluetooth Low Energy (BLE)How Apple and Google’s Bluetooth Contact Tracing Framework Actually Works
Explore how Bluetooth contact tracing works, its technical foundations, and the privacy tradeoffs. Learn what BLE enables, what it doesn’t, and how tracing apps were designed to scale.
 Software Tools & Techniques
Software Tools & TechniquesWhy Re-Signing iOS Apps is Better than Recompiling
Maintain binary integrity and streamline compliance by modifying app metadata, assets, and provisioning profiles without recompiling, reducing risk and ensuring consistency across builds.
Dive into our complete collection of articles, guides, and resources.