Introduction
Firmware plays a critical role in connected medical devices, but it can’t stand alone. It has to function within a complex, regulated system that includes hardware, mobile apps, cloud infrastructure, and safety-critical workflows. Getting those components to work together, on time and within budget, takes careful coordination.
It becomes even more challenging when firmware is developed and tested without considering how it fits into the larger system. When integration is treated as a late-phase task or requirements are defined in silos, issues emerge that can affect not just the system, but patient safety.
Integration failure isn’t an obscure risk. It’s a well-known one that often goes under-addressed until it’s too late.
What We’ll Cover
We’ll break down how firmware integration failures happen, even when you’ve planned carefully and staffed the right team. You’ll see how early disconnects in development can create costly ripple effects across connected medical systems. Then, we’ll walk through the process we use at Punch Through to reduce integration risk at every phase, from project planning and system design to CI pipelines and automated testing.
If you’ve ever experienced late-stage surprises during integration, this guide will show you how to spot those risks earlier and avoid them altogether.
Why Early is Best When it Comes to Integration
Integration issues don’t just exist on paper—they surface in the real world through missed timelines, rework, or even patient risk.
To show what’s at stake, here’s a scenario that came dangerously close to reality in one of our high-stakes medical device projects. It highlights how even small assumptions or missed handoffs can escalate into system-wide failure.
To illustrate what’s at stake, imagine a scenario like this:
A medical device company spends millions over five years developing a next-generation implantable device with BLE connectivity for remote management and firmware updates. The team defines strict requirements around command sequences, image formats, and authentication. The release candidate is tested, validated, and ultimately deemed fully functional. Implantations begin.
Sometime later, a new firmware version is issued to add minor quality-of-life improvements. But during a routine update at a clinic, a field engineer accidentally uploads firmware intended for a different device in the system. Because both devices use the same root signing key, the implant accepts the update image despite it being incompatible. The device bricks and surgical removal is required.
The damage doesn’t stop there: production halts, confidence erodes, and regulatory concerns surface. All because the system couldn’t distinguish between what should be allowed and what could be allowed.
This isn’t just a cautionary tale, it’s a scenario we’ve seen nearly play out in real-world projects. And it reflects a broader challenge that medical device teams face. How to design and develop firmware that will behave correctly not just on its own, but in the real-world ecosystem it lives in.
So where does this risk come from? And why is it so often underestimated or missed entirely, even by experienced teams?
Want a broader look at early firmware integration across industries? Check out Garin’s article.
What Causes Integration Risk?
Even with experienced engineers and detailed planning, missing or ambiguous requirements are a common source of integration failure. But they’re just one piece of the puzzle.
Hidden Assumptions & System Drift
Unrecognized ambiguity, implicit assumptions, and inevitable system evolution during development often lead to unforeseen issues that don’t surface until everything comes together—when it’s often too late or too expensive to fix cleanly.
Parallel Workstreams Without Coordination
These risks are often baked into how development is structured. Firmware, hardware, and software are often built in parallel workstreams, which can accelerate timelines—but without careful alignment, integration points become bottlenecks where incompatibilities and miscommunications pile up.
A Systemic Challenge, Not a Team Failure
This challenge isn’t unique to any one team or company—it’s a systemic tension in how connected medical devices are developed. And without a process that actively accounts for integration risk throughout the lifecycle, even small missteps can snowball into system-wide failures.
The Impact of Ignoring Integration Risk
Left unaddressed, integration risk can delay timelines, inflate budgets, and compromise patient safety. But it doesn’t have to be that way. With the right process in place—one that treats integration as a continuous priority rather than a final milestone—these risks can be anticipated, managed, and significantly reduced.
That’s the mindset we bring to every project.
Our Perspective on Managing Integration Risk
At Punch Through, we’ve spent over a decade helping medical device companies build firmware that integrates seamlessly into complex systems. While every project is unique—defined by its architecture, regulatory pathway, and product roadmap—we’ve seen clear patterns emerge across hundreds of engagements.
Successful integration doesn’t happen by accident. It requires a development process that prioritizes system-level alignment at every stage.
Our approach is designed to do exactly that. We tailor each engagement based on the current state of the system, the product’s maturity, and our client’s internal capabilities. But across all projects, we’ve identified a few consistent strategies that are critical to reducing integration risk:
- Start with aligned requirements
In the early stages, close collaboration on detailed requirements ensures that the firmware will align with the broader system’s expectations. - Build feedback into the process
Once development begins, automated CI pipelines, unit testing, and integration testing provide fast feedback on whether the firmware behaves as expected—and continues to do so as it evolves. - Integrate early and often
Throughout development, we integrate early and often. Frequent deliverables and close coordination with other system components enable early end-to-end testing and help burn down long-term integration risk before it compounds.
In the sections that follow, we’ll walk through how this approach takes shape across each phase of a project—from initial planning through final delivery—and how it supports the development of connected medical devices that are robust, reliable, and truly ready for the field.
Managing Integration Risk Throughout the Development Process
We structure every engagement around four key phases: project planning, architecture and design, development, and completion.
But when it comes to managing integration risk, these phases don’t carry equal weight. Most of the active risk mitigation work happens during development—but the success of that work hinges on what happens before and after it.
Here’s how we approach each phase with integration in mind.
Project Planning Phase
Before any code is written, we work with clients to establish a shared understanding of the system, its constraints, and its risks. While this phase is often part of the business development process, it’s also where integration planning begins—mapping the path ahead so we can anticipate where things might go off track.
Understand the system early
At this stage, Punch Through guides potential clients through our project planning process. It’s an opportunity for our engineering team to build a baseline understanding of the system’s current state and the scope of the proposed development effort. Through conversations with key stakeholders, we gather context on system behavior, known bugs, risk areas, and integration pain points that will need to be addressed.
Review documentation and surface ambiguity
Whenever possible, we review existing design documentation, requirements, and firmware to get a fuller picture. This step plays a crucial role in accurately defining both the effort required and the potential system interactions that could introduce integration risk later on.
Define effort, risk, and alignment in the SOW
The main deliverable from this phase is a detailed Statement of Work (SOW). It outlines the proposed engagement in terms of workstreams, milestones, and estimates for time and budget and it includes an analysis of any known unknowns or technical risks that may impact those projections.
Key Takeaway: Even before a client selects us as their vendor, we’re thinking about integration: defining the key touchpoints between systems, uncovering ambiguity, and putting a structure in place to reduce risk from the start, especially in regulated contexts where the cost of failure is high.
Architecture and Design Phase
When it comes to integration risk, architecture decisions have a lasting impact. They define how different parts of the system will communicate, what assumptions will be baked into the firmware, and how easily changes can be made down the line. And in medical device development, those decisions are harder to unwind once verification and documentation are in motion.
Start with architecture in greenfield projects
That’s why every Punch Through project begins with a focus on design, but what that means depends on the maturity of the system.
For greenfield projects, we often recommend a dedicated architecture phase. This gives our team time to deeply understand the system context, use cases, and user expectations—and to define the architectural foundation that will support integration across devices, apps, and infrastructure. (For a deeper dive into this process, see our BLE Connectivity Architecture Guide.)
Adapt design work for established systems
In other cases, the system architecture may already exist, or be partially defined. In these situations, design becomes an ongoing, iterative activity throughout the engagement, especially as new features are introduced or existing components evolve.
Design for integration-readiness
Regardless of the project’s starting point, our design process focuses on integration-readiness. We identify key interfaces, define clear boundaries between subsystems, and flag areas where firmware behavior could diverge from system expectations. By catching those mismatches early, we help avoid rework during formal verification or worse, post-deployment.
Note: In medical device development, design isn’t just about what the firmware does, it’s about ensuring it can do it in context, without introducing risk.
Firmware Development Phase
With baseline context established, key requirements defined, and potential risks identified, the firmware development phase can begin in earnest. Development is where the rubber meets the road for risk mitigation, so many of the code quality and risk management strategies employed by Punch Through engineering teams are focused on reducing integration risk during this stage of a project.
Below, we break down the specific practices that help us manage that risk and ensure firmware not only works, but works reliably as part of a regulated, safety-critical system.
Integration Frequency: Reducing Drift Over Time
One of the key components of risk mitigation is integration frequency. Strategies like unit and integration testing, close collaboration, and frequent deliverables are all aimed at reducing the amount of time between each integration point—thereby minimizing the risk at each point. The graphics below illustrate the relationship between integration risk and integration frequency. In the first graphic, the project has only one integration point at the end, and deviation from the product vision is bounded by a cone of uncertainty.
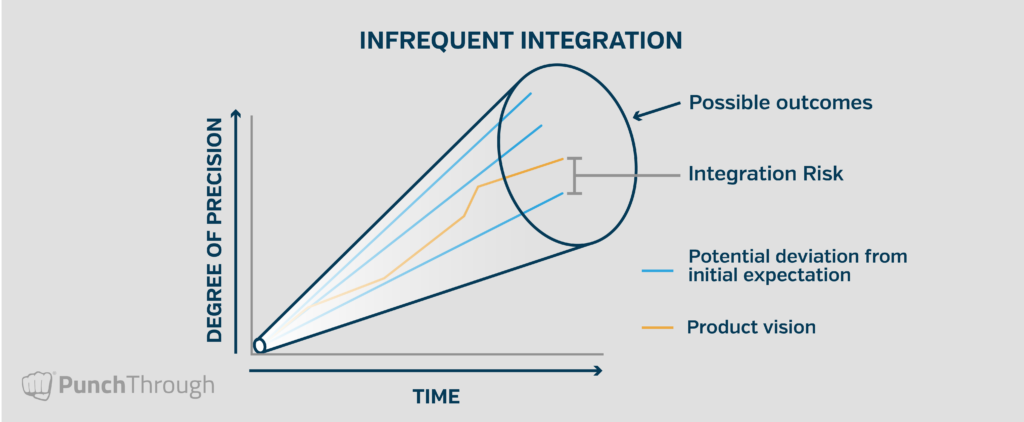
When the amount of time between integration points increases, so does the risk of deviation from the product vision. The distance between the final deliverable and the product vision represents the realized integration risk.
By integrating early and often, any change or drift in any part of the system that breaks compatibility is quickly discovered and resolved. This proactive approach reduces the potential for integration problems at the end of a project by creating frequent checkpoints—opportunities for development and the product vision to realign. The following graphic illustrates a firmware development project with regular integration points and realignment over time.
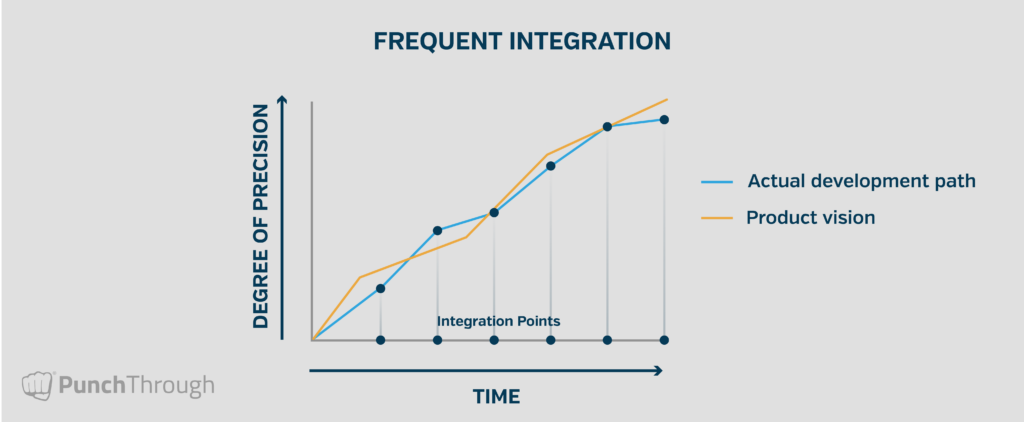
When integration is left until the end, deviation from the ideal outcome can be significant—often resulting in severe delays, especially in regulated environments. Conversely, by building integration into the firmware development plan from the start, Punch Through shortens the feedback loop and burns down integration risk continuously. On one recent project with a large number of unknowns, our team implemented integration points every 70 hours. That frequency helped ensure new information could be incorporated quickly into subsequent development phases.
Agile Delivery and Continuous Feedback
Punch Through’s Agile project management approach supports this fast, flexible cadence. Our embedded software teams iteratively design, develop, test, and release firmware while incorporating continuous feedback from clients and collaborators.
This process accelerates decision-making and keeps subsystems aligned as requirements evolve. For medical devices—where teams are often navigating regulatory constraints and shifting product needs—Agile’s responsiveness is key to managing integration dependencies across hardware, mobile, and cloud components.
The Agile lifecycle graphic below illustrates how these practices come together in each sprint or feature iteration.
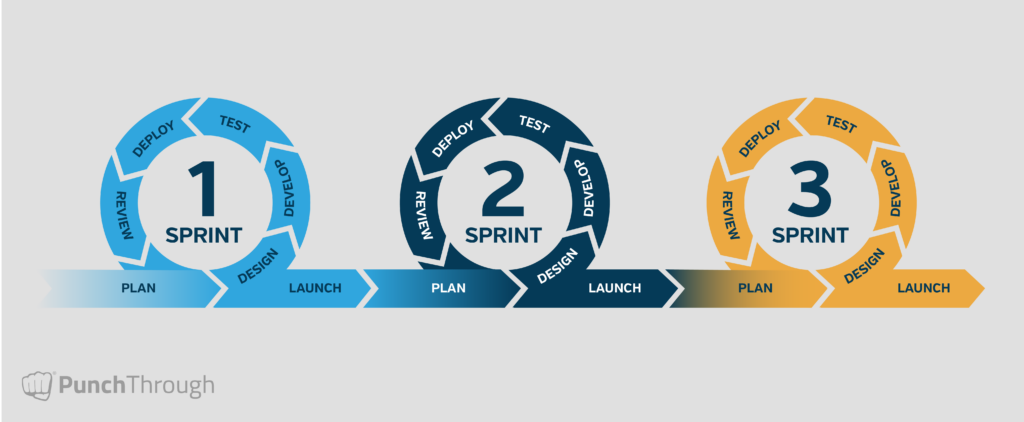
Related Reads: For more detail on our project management approach, see How We Manage Projects at Punch Through and How to Use Agile Frameworks in the Medical Device Industry.
Test Automation as a Risk Management Tool
Testing and automation are essential to verifying that firmware behaves as expected—not just functionally, but in the context of the full system. By automating as much of the testing process as possible, we’re able to catch and correct regressions early, without waiting for formal test cycles or end-stage validation.
This is especially critical in medical device projects, where firmware is often part of a broader, regulated system. Automated testing gives us confidence that new changes won’t break existing functionality—or introduce risk when firmware is integrated with other system components.
Configuration Management and CI Setup
Reliable integration also depends on a consistent build environment. That’s why one of the first things we do in a new project is set up automated linting, builds, and unit tests within a CI pipeline. This ensures the firmware builds the same way across development environments—reducing the chance of configuration-related bugs and avoiding surprises during integration with test rigs, mobile apps, or production hardware.
In medical device contexts, where traceability and reproducibility are essential, this kind of infrastructure also supports documentation and validation efforts later in the development lifecycle.
Unit Testing for Reliability and Design Discipline
We incorporate unit testing directly into firmware development not as an afterthought, but as a parallel activity that helps enforce interface contracts, expected behaviors, and edge case handling from the start.
By surfacing regressions immediately, unit testing reduces the risk of undetected issues making their way into integrated builds. This is especially important in safety-critical environments where unexpected behaviors, even small ones, can affect usability, compliance, or patient outcomes.
Unit testing also encourages sound design. The need for testable, modular firmware pushes developers toward cleaner interfaces and minimal reliance on global state, both of which make integration smoother.
For example, during a recent implantable medical device project, our team used Zephyr’s ZTest and GitHub Actions to run unit tests on-device with each pull request, while non-hardware tests ran in a Posix virtual environment. This allowed us to test real-world interactions early, improving confidence in hardware/firmware compatibility.
Integration Testing with Hardware in the Loop
While unit testing covers module-level correctness, integration testing ensures those modules work together, especially when real hardware is involved.
We develop integration tests in parallel with features, using hardware-in-the-loop (HIL) setups whenever appropriate. These tests validate system-level behaviors, define expected command sequences, and trace directly to requirements—making them critical not just for development, but for verification planning as well.
In one of our longest-running medical device projects, we implemented a Jenkins server connected to physical hardware, integrated with Bitbucket. It automatically ran the full integration test suite on every commit to develop, master, or any jenkins-prefixed branch. Tests were written in Python with Pytest, and results were cached for long-term review.
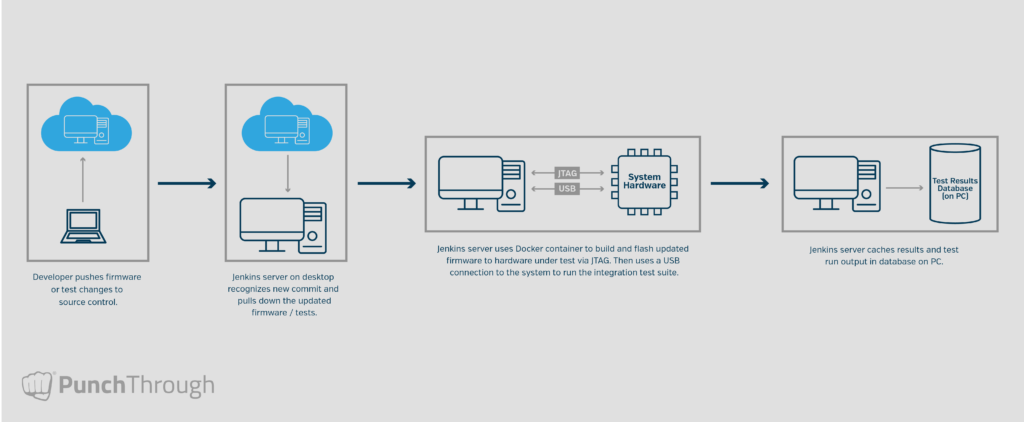
By baking integration testing into our CI infrastructure, we ensure that every change is evaluated for system-level compatibility before it can be merged. This creates a reliable feedback loop and helps prevent subtle, system-level failures from slipping through.
Transparency and Collaboration Throughout
Even with strong infrastructure in place, integration risk is ultimately a human problem: it emerges when communication breaks down, priorities shift without alignment, or assumptions go unvalidated.
That’s why we prioritize transparency and collaboration throughout the development phase. Weekly or biweekly status meetings keep teams aligned and surface risks early. When new blockers arise or priorities shift, we work closely with clients to adjust while maintaining visibility across the system.
We also deliver builds at the end of each sprint, or after completing a major feature, for client-side integration testing. This regular cadence of shared progress ensures that firmware doesn’t become siloed, and that issues are addressed before they escalate.
Key Takeaway: In medical device development, the cost of discovering a misalignment late is high. That’s why we treat integration not as a milestone, but as a continuous priority throughout development.
Project Completion Phase
The criteria for completing a project are defined in the SOW at the outset and can vary widely depending on the needs of the client and the maturity of the product.
Tailor deliverables to product maturity
In some cases, the final deliverable is an official release intended for FDA submission. In others, the engagement may focus on a specific feature set that will be further developed or integrated downstream. Regardless of the endpoint, our goal is always the same: to ensure that the firmware we deliver integrates smoothly into the broader system and can be supported effectively moving forward.
Deliver more than firmware
As part of every handoff, our engineering team provides not only the firmware itself, but also the supporting infrastructure developed along the way—automated test suites, documentation, and configuration details. These assets give internal teams the tools they need to maintain, extend, and validate the firmware without reintroducing risk.
Support future changes and maintain reliability
This is especially important in the medical device space, where traceability, reproducibility, and post-market support are essential. A successful handoff isn’t just about meeting the spec—it’s about preserving the system-level reliability we’ve worked to build throughout the project.
And while our development process is built to deliver firmware that integrates cleanly, we recognize that things evolve. If integration issues arise post-delivery due to new system changes, updated requirements, or other shifts, we’re always available to support resolution and ensure the system continues to perform as expected.
Note: Integration risk doesn’t end when a project does. That’s why our handoff process is designed to maintain alignment, transparency, and momentum, even after the last commit.
When to Bring in a Partner
Not every team needs outside support, but when it comes to firmware development for connected medical devices, the complexity of integration can make external expertise invaluable. The right software and technology partner can help navigate these challenges and ensure a smoother launch, without the pain of delays or costly errors.
Bringing in an experienced firmware team doesn’t mean relinquishing control; it means supplementing your internal resources with specialized embedded systems expertise and a development process tailored to address integration risks head-on.
Here are some signs that might indicate when external help is needed:
- First-time development of connected firmware for a medical device
- Late-stage integration challenges that have impacted previous projects
- Need for confidence in system behavior before verification or submission
- Drifting alignment between firmware and other system components (mobile, cloud, hardware)
- Pressure to deliver quickly, but a commitment to avoiding shortcuts that can introduce risk
Whether it’s a focused engagement to address specific challenges or a more comprehensive partnership, the goal is always the same: to help you ensure that your firmware integrates seamlessly, is reliable, and functions as expected in the real-world system.
Integration Isn’t a Phase, It’s a Discipline
Integration issues aren’t always loud. Sometimes they show up as subtle misalignments, intermittent bugs, or inconsistencies that surface only when the system is under pressure—during verification, in the field, or in the hands of a patient.
In medical device development, even small oversights can lead to delays, rework, or patient risk. And the further along those issues are discovered, the more expensive and disruptive they become.
That’s why we recommend an approach that treats integration not as a final milestone, but as a guiding principle throughout development. From early planning and architecture to testing infrastructure and team alignment, reducing integration risk requires a process built for visibility, adaptability, and real-world system context.
This mindset has shaped how we work through hundreds of projects and across a wide range of connected medical devices. We’ve seen what happens when integration is treated as an afterthought and how much smoother things run when it’s prioritized from the beginning.
Getting firmware to work is only part of the job. Making sure it works as part of a larger, regulated, connected system is where the real challenge, and real value, lies.