Cloud communication plays a critical role in many connected medical devices, supporting telemetry uploads, remote configuration, and firmware updates. This data might include device performance metrics, patient measurements, commands to update device settings, or OTA firmware notifications. Because many devices operate intermittently or rely on low-power wireless protocols, they often use a mobile app or gateway as an intermediary to the cloud.
These systems must account for intermittent connectivity, latency, and the need for secure, authenticated data transfer. This article offers a practical overview of cloud communication architectures used in connected device ecosystems, with a focus on reliability, security, and architectural trade-offs. Whether you’re planning a new system or refining an existing one, our aim is to help technical leaders make informed design decisions.
To understand the architectural decisions that follow, it’s important to start with how data actually moves between device, app, and cloud.
Understanding the Communication Path
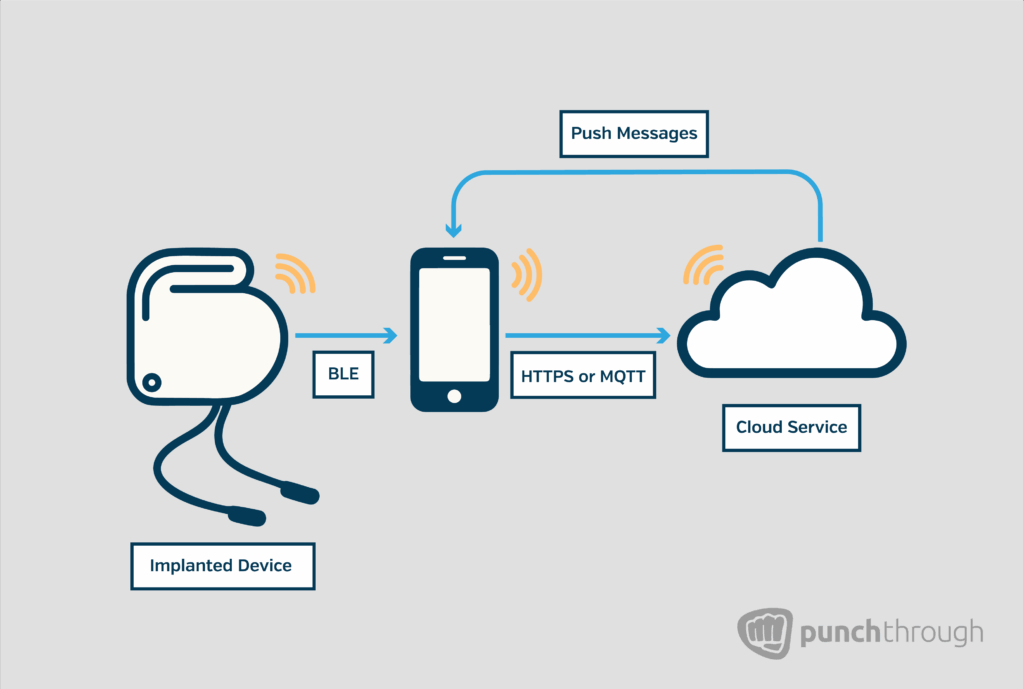
In connected medical devices, data often flows from a low-power peripheral such as an implanted or wearable sensor through a mobile app to the cloud. Whether it’s telemetry, commands, or firmware updates, this communication path must function securely and reliably, even when devices are intermittently online.
This architecture introduces unique constraints. Implanted and wearable devices rely on Bluetooth for short-range transfer and delegate cloud connectivity to a mobile intermediary with Wi-Fi or cellular access. While common, this indirect and asynchronous flow introduces reliability and security challenges that cloud architecture must account for directly.
Because the data involved is often sensitive, protecting its confidentiality, integrity, and access is not optional. It is a regulatory and clinical requirement. Design decisions at this communication layer must address delivery guarantees, failure recovery, and secure authentication across the entire path: from device to app to cloud.
Choosing the Right Communication Method
Once the mobile app receives data from the device, it needs a way to send that data to the cloud or retrieve updates and commands intended for the device. The communication method you choose will affect performance, latency, security, and how resilient your system is to connectivity issues.
The next few sections break down three common approaches to app-to-cloud communication in connected medical devices: web APIs, MQTT-based messaging, and push notifications. Each comes with trade-offs and is better suited to specific use cases and system constraints.
Web APIs
Calling a web API is often one of the simplest and most familiar ways for a mobile app to exchange data with the cloud. It’s straightforward to implement, widely supported, and flexible enough for a variety of use cases, especially when paired with JSON message formats and HTTPS for secure communication.
To build this kind of interface responsibly, though, you’ll want to think beyond just sending and receiving data. The security and reliability of every request matters, especially in connected health environments where data integrity is critical.
On the client side, all requests should use HTTPS with the latest TLS version to ensure data in transit is encrypted. On the server side, make sure each request goes through strong authentication and authorization checks, and that you’re validating incoming data early before it’s processed further.
Most modern web frameworks support schema validation and can help enforce strict data formats, which reduces error-handling downstream. These same schemas can often be used to generate OpenAPI docs, making it easier for your mobile team to understand and work with your endpoints using tools like Swagger or Redoc.
When it comes to token management, follow the same standards you’d use for passwords: store tokens as hashed values (not plain text), and implement expiration and revocation mechanisms to minimize risk. Tokens should be short-lived and easily renewable.
A reliable, off-the-shelf approach is to use OAuth 2.0 with Authorization Code Flow and PKCE. This gives you token-based authentication without having to roll your own solution and helps mitigate risks like cross-site request forgery. With this flow, the mobile app obtains a short-lived access token (often valid for around an hour), and uses a refresh token to extend the session without requiring the user to log in again.
IoT Services (MQTT)
If your mobile app needs to handle a near real-time stream of data or manage messages that may arrive while the app is offline, an IoT service using MQTT, like Azure IoT Hub, can be a strong fit.
MQTT is designed for scenarios where devices aren’t always connected. It allows messages to be queued on either side (client or server) and then delivered when the receiver is back online. That flexibility makes it especially useful in medical device workflows where connectivity can be spotty or unpredictable.
When a connection is available, MQTT delivers messages quickly and reliably. And if you’re using a cloud provider’s IoT platform, you’ll usually get access to mobile SDKs that abstract away much of the protocol’s complexity. That means your mobile team can work with MQTT without needing to learn the ins and outs of the spec itself.
Like with web APIs, MQTT messages often use JSON payloads, so your app’s data-handling logic can stay consistent across communication methods. The key benefit here is resilience. MQTT gives you a built-in way to handle temporary disconnections without losing critical data in transit.
Push Notifications
Both iOS and Android support push notifications from cloud-based systems, useful when the mobile device is online but the app isn’t currently active. While push notifications don’t typically carry much data, they’re a handy way to prompt the app to launch and take further action, like fetching new information or initiating a background task.
Services like Firebase, Azure Notification Hubs, or AWS SNS help deliver these notifications using platform-specific protocols under the hood. They take care of the heavy lifting, so you don’t have to manually manage the complexities of mobile OS messaging systems.
In connected medical devices, push notifications are often used to alert patients when new settings are available, or when it’s time to install a firmware update. That said, they’re not foolproof. Notifications depend on a stable internet connection and can sometimes be delayed or lost entirely.
For anything critical, don’t rely on push alone. Instead, treat notifications as a nudge and back them up with fallback logic. Your mobile app should check in with the server at the right moments (like app launch or resume) to make sure it hasn’t missed any important messages or commands.
Building in Security from the Start
Security should be baked into every layer of your device-to-cloud communication, not bolted on at the end. At a minimum, all data in transit must be encrypted using strong protocols like HTTPS with TLS 1.2 or above. For MQTT-based systems, TLS should be used to secure the connection between device and server. And since push notifications rely on platform-managed infrastructure, both iOS and Android require HTTPS for secure delivery out of the box.
But encryption alone isn’t enough.
Two critical concepts—authentication and authorization—need to be clearly defined and properly implemented. Authentication ensures that both the device and cloud know who they’re talking to. Authorization ensures that each party is allowed to perform the action it’s requesting. In most systems, this means leaning on certificate-based authentication or public key infrastructure (PKI). For added assurance, consider using mutual TLS (mTLS) to validate both ends of the connection.
For implanted medical devices, there’s an additional challenge: communication often passes through a mobile phone acting as a relay. To protect against man-in-the-middle attacks, these systems typically benefit from a secure tunnel protocol. One where the message payload is encrypted in a way that only the cloud and the device itself can decrypt. That way, even though the mobile app is in the loop, it can’t read or modify the contents in transit.
These layers of protection aren’t just for compliance, they’re essential to patient safety, system integrity, and trust in your connected solution.
Engineering for Real-World Reliability
Reliable communication is essential in connected medical devices. When data doesn’t reach the cloud, it can create gaps in patient records, interfere with clinical decisions, and complicate compliance.
Designing for reliability means accounting for real-world conditions like intermittent connectivity, limited device resources, and cloud systems that may not always be available. Supporting message queuing, acknowledgments, and retry logic is essential, particularly in systems where devices may be offline or out of range for extended periods.
Message Queues with MQTT
A common way to build resilience into device communication is by using a message queuing protocol like MQTT, often through cloud services such as Azure IoT Hub or AWS IoT Core. These platforms can provide guarantees like at least once delivery, where messages are retried until the device confirms receipt.
But for device-to-cloud communication, reliability often hinges on how well the device handles being offline. It’s critical that the device is equipped to:
- Queue messages locally: Store unsent data until a connection is restored.
- Wait for acknowledgment: Only clear messages from the queue once they’ve been confirmed as received.
- Retry intelligently: Implement a strategy to resend messages when the network comes back without draining battery or flooding the system.
These patterns ensure that temporary outages don’t turn into permanent data loss.
Web APIs
HTTP-based APIs can also support reliable communication, but the bar is higher. Because HTTP is synchronous, the client and server must both be online and reachable at the same time. That makes network hiccups more disruptive unless deliberate reliability measures are in place.
On the client side, consider:
- Retry policies: Use exponential backoff (with jitter) to avoid overwhelming the server or killing the battery.
- Circuit breakers: Temporarily stop retries if repeated failures indicate a broader issue.
- Timeouts: Set sensible limits so the app doesn’t hang indefinitely.
- Fallback strategies: Cache configuration data locally or use sane defaults when a server call fails.
- Offline queuing: Store unsent data for later transmission, similar to the MQTT model.
- Background processing: Run non-UI tasks (like Bluetooth communication or retries) in the background to maintain responsiveness.
On the server side, reliability patterns include:
- Robust error handling: Gracefully handle malformed requests, service hiccups, or temporary overloads. Use clear status codes like 503 Service Unavailable to help clients respond appropriately.
- Idempotency: Prevent issues from retries by designing endpoints that safely handle duplicate requests, often using unique transaction IDs.
Choosing the right approach depends on your product’s environment and data criticality. MQTT-based systems offer more built-in resilience, especially when connectivity is unpredictable. But if you’re working with HTTP APIs, you’ll need to deliberately engineer reliability into both ends of the system.
In either case, don’t treat reliability as a later-phase concern. It’s a foundational part of delivering a trustworthy, effective medtech solution.
Why Architecture Expertise Matters
Designing secure, reliable communication between a connected device and the cloud isn’t just a matter of implementing the right protocol. It requires system-level thinking that accounts for regulatory constraints, real-world failure modes, cross-platform behavior, and future scalability.
These kinds of decisions often cut across engineering disciplines—firmware, mobile, cloud, and security—making it difficult for internal teams to own every detail without support. Bringing in an experienced architecture partner can help expose hidden risks, validate design decisions early, and streamline development by aligning everyone around a coherent strategy.
The most effective partnerships aren’t about handing off work. Instead, they’re about collaborating with teams who understand both the technical depth and regulatory context required to get it right.
Conclusion
Communication architecture decisions carry long-term consequences for connected medical devices, from how reliably data moves through the system to how easily it scales and stays compliant over time. Getting it right requires more than implementation; it requires intention.
If you’re working through these decisions and want to explore more, we’ve published additional resources on BLE, system architecture, and cloud communication for connected medical devices. And if you’re looking for a second opinion or strategic input, we’re always open to a conversation.